Malicious contributors. FOCI. Vulnerabilities. Hidden secrets. Poor code quality. Bad licenses.
Go (way) beyond software composition analysis.
Did They Really Say That?
Yep. Bulletproof Trust has wow’d customers since the beginning with it’s deep and detailed threat intelligence. Here’s what they have to say:
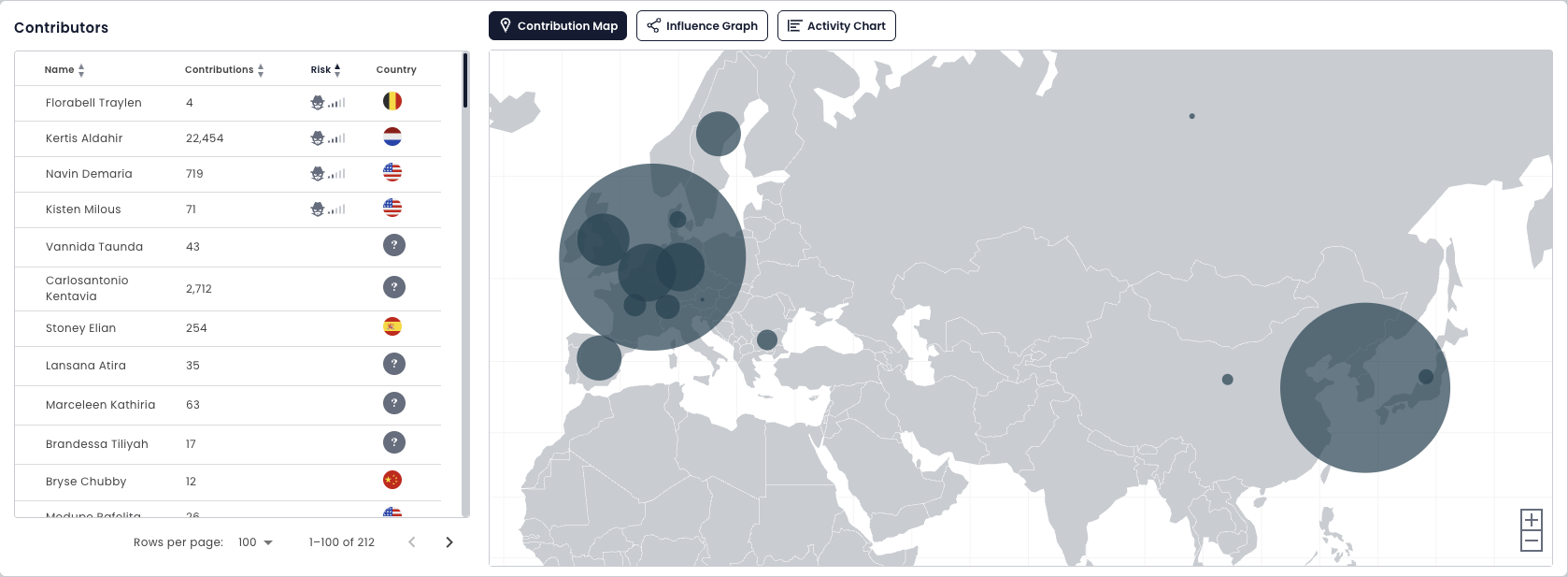
“Bulletproof Trust stands out as one of the few tools offering any visibility into foreign influence over the software supply chain, a capability not currently claimed by other tools.” — Jim B.
“These folks are the real deal (all intel community) and have built some very impressive capabilities to address the national security concerns surrounding software supply chains.” — Jeff G.
“If I were to build a dashboard for supply chain risk, this would be it.” — Rich M.

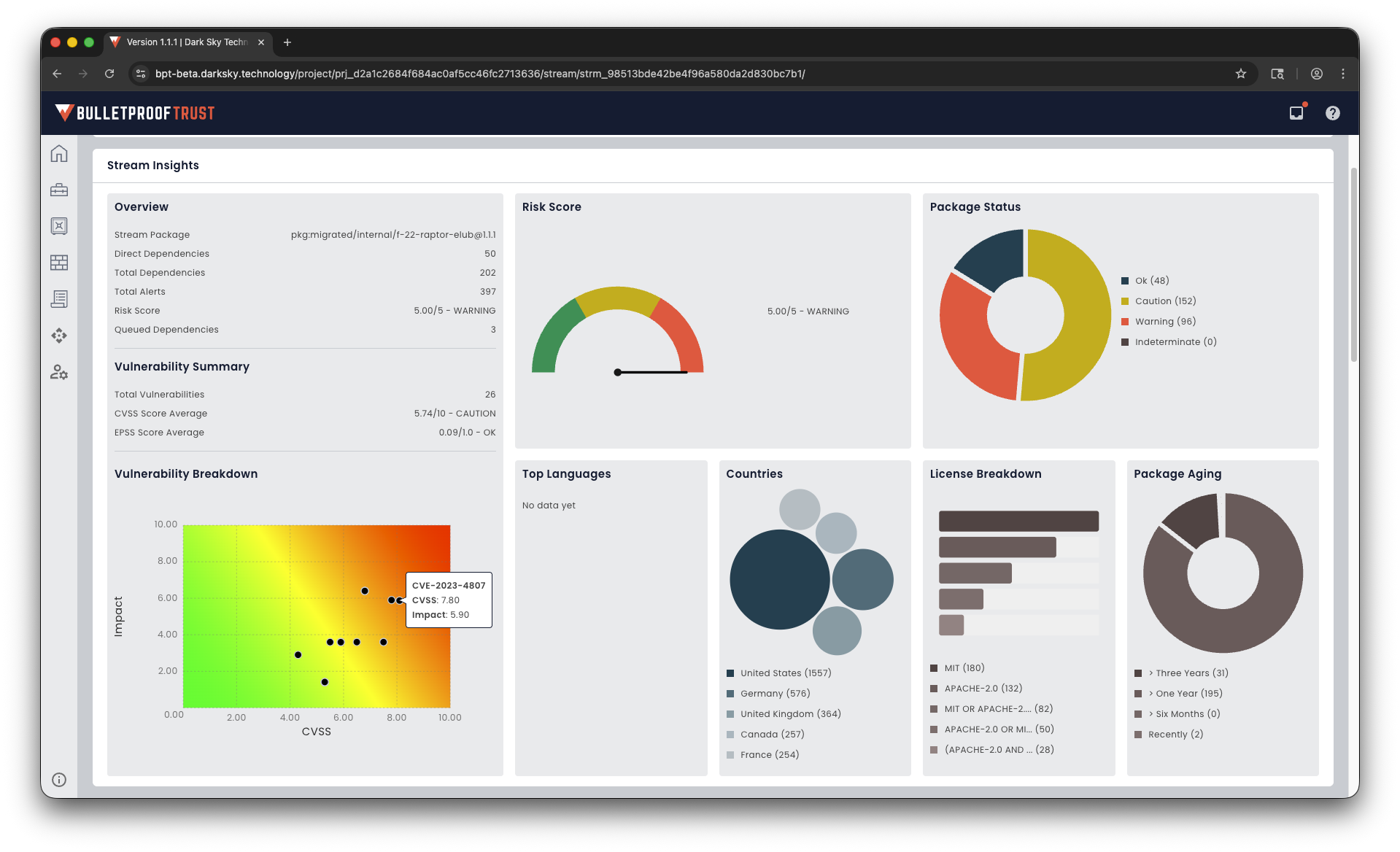
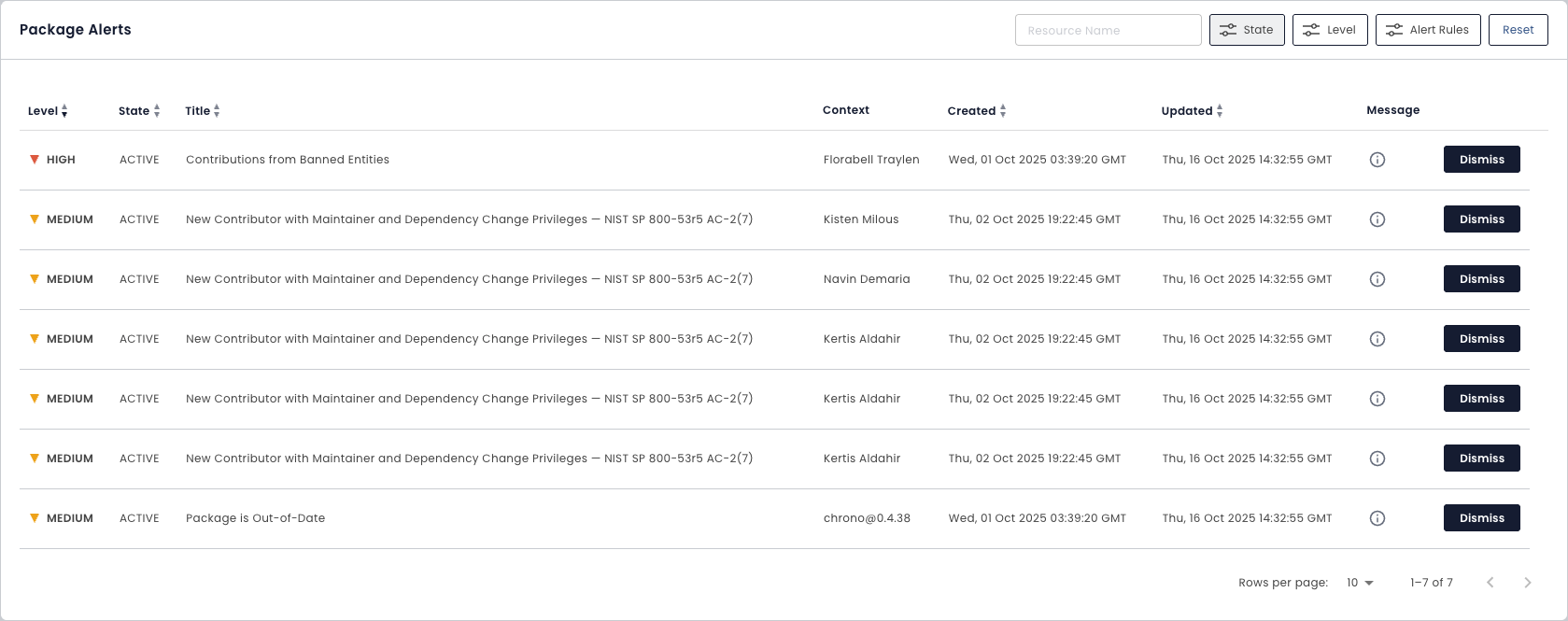
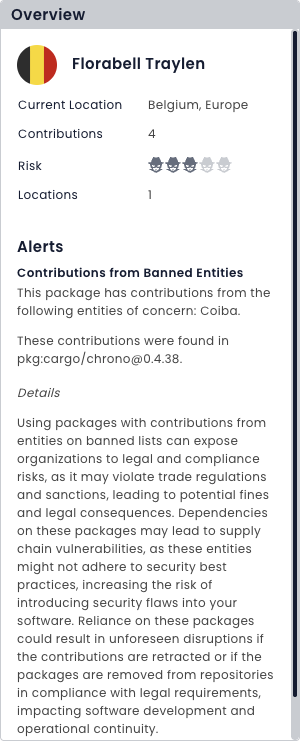
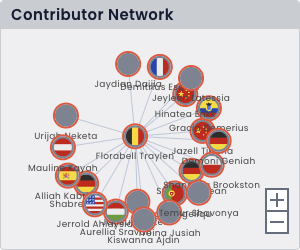
Map Risks Across Your Enterprise
Risks come in many forms. Bulletproof Trust uncovers vulnerabilities, license and copyright issues, code maintainability problems, hidden secrets, and much, much more.
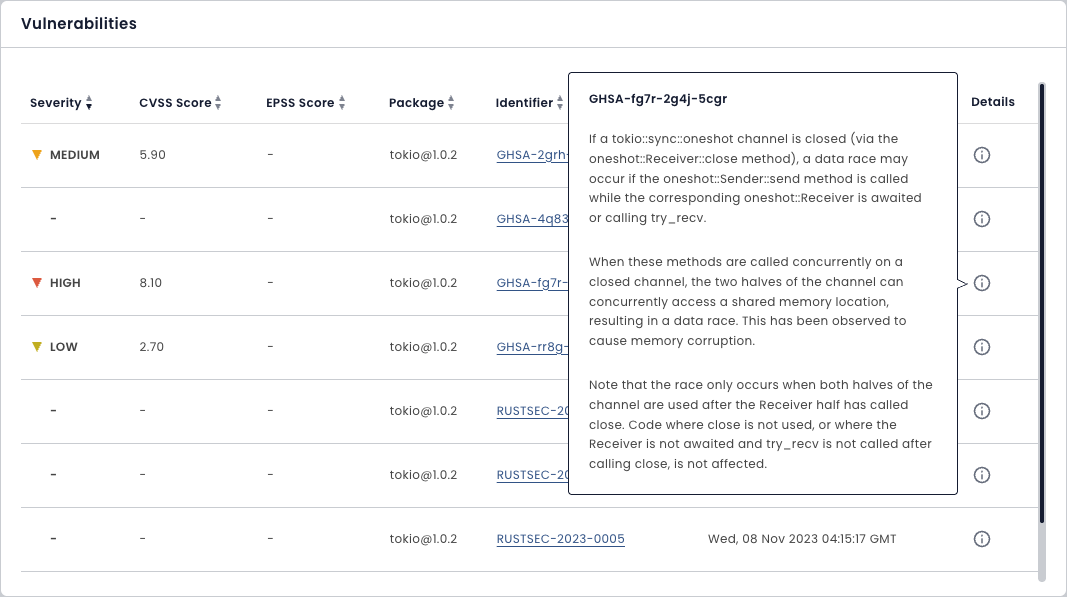
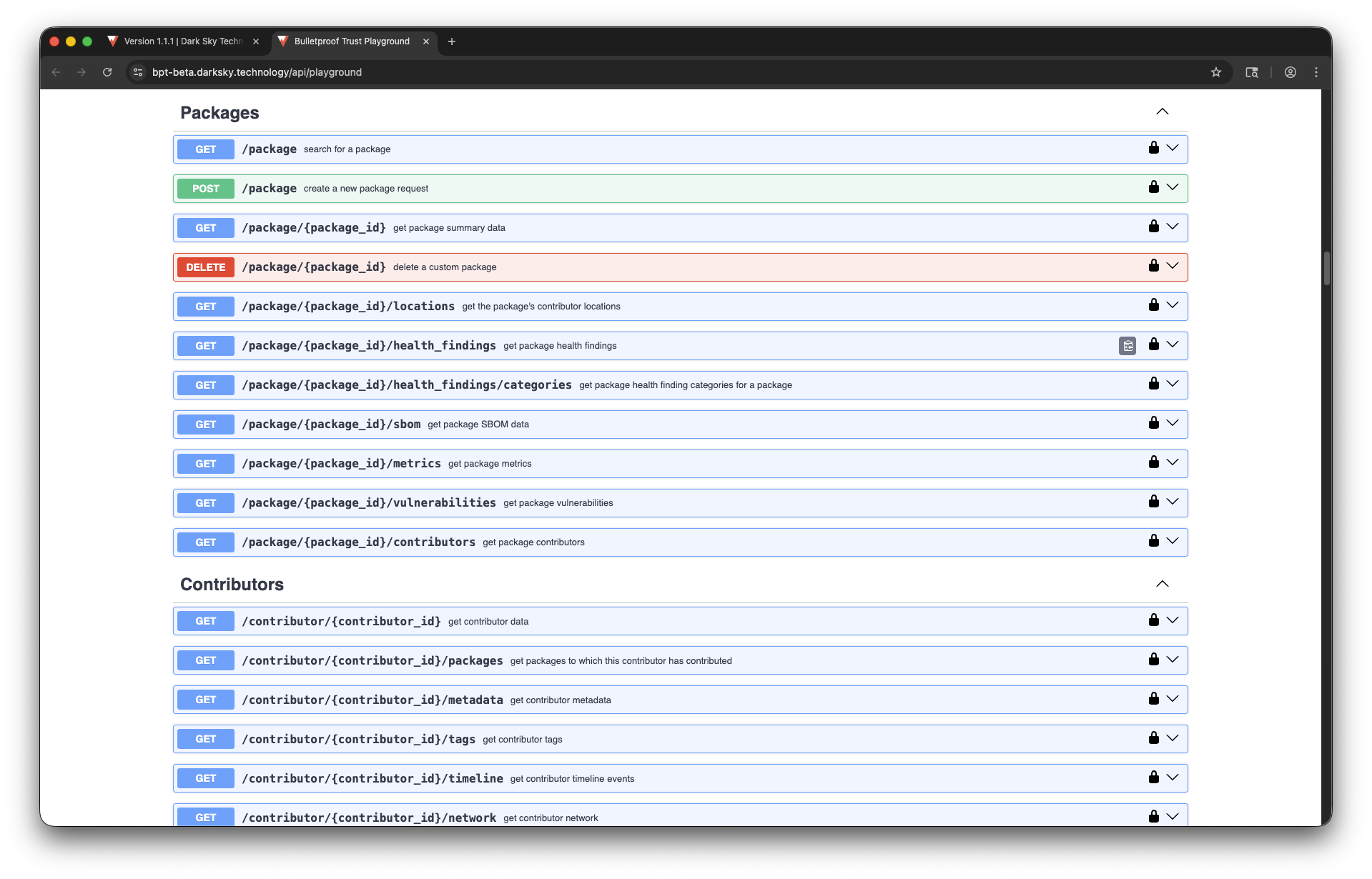
Continuous Vulnerability Monitoring
Bulletproof Trust scans every package and every package dependency (and all their dependencies) in your SBOM for vulnerabilities continuously from nearly 40 vulnerability databases including the National Vulnerability Database, GitHub Security Advisories, and more.
No more wondering if a vulnerable package affects your system.
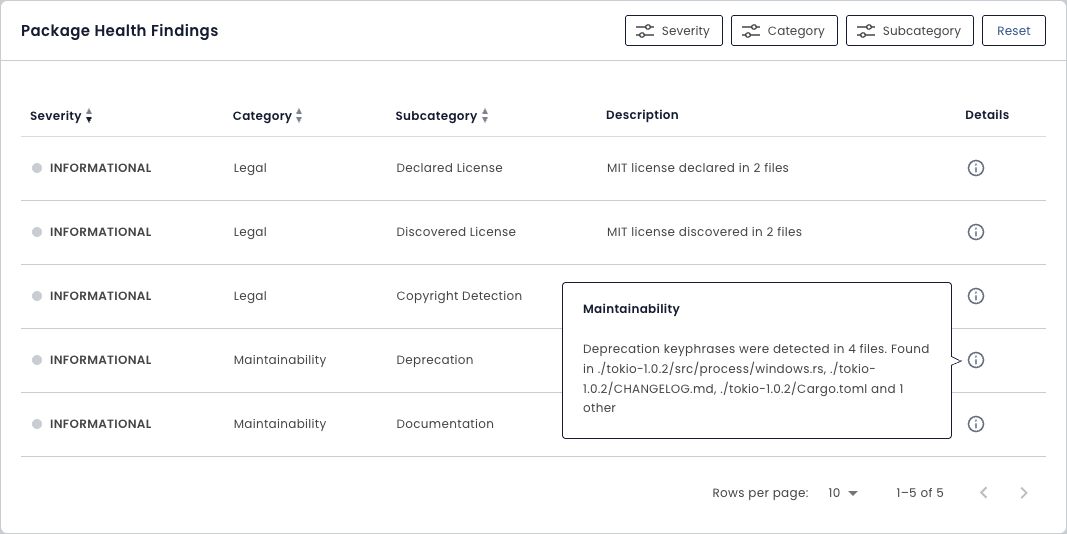
Deep Package Health Monitoring
There’s more to package health than just vulnerabilities. Bulletproof Trust analyzes every package and dependency for code quality or deprecation notices that could cause maintainability problems, license mismatches and copyrighted code that could give you legal troubles, hidden secrets like API keys or credit card numbers, and more.
Finally. Use open-source software with confidence.


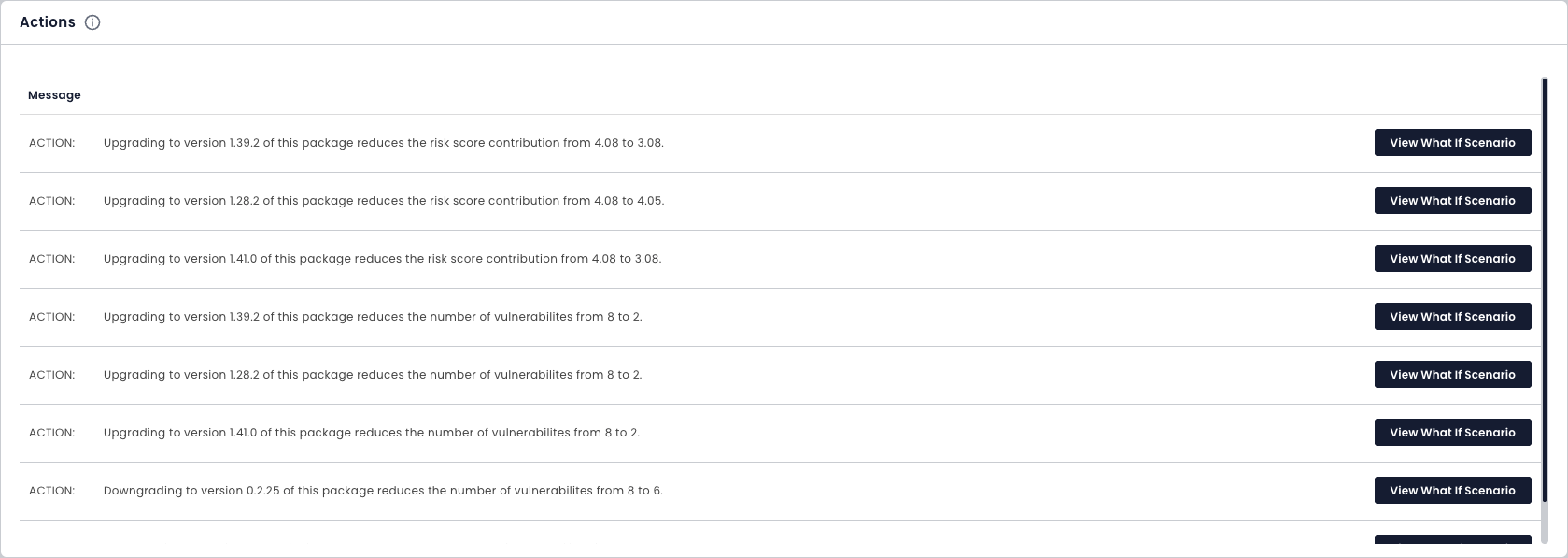
Threat Intelligence (Without the False Positives)
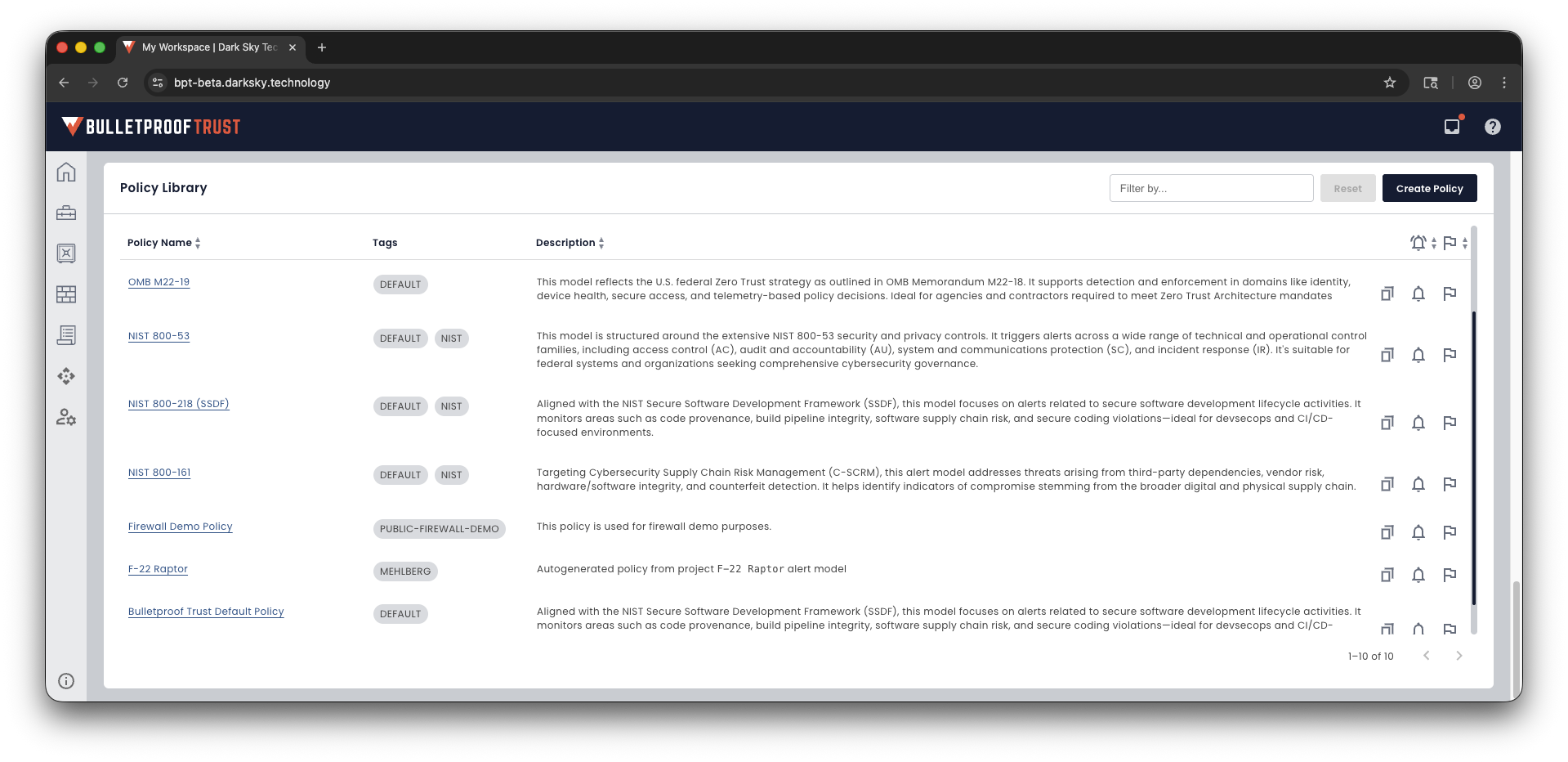
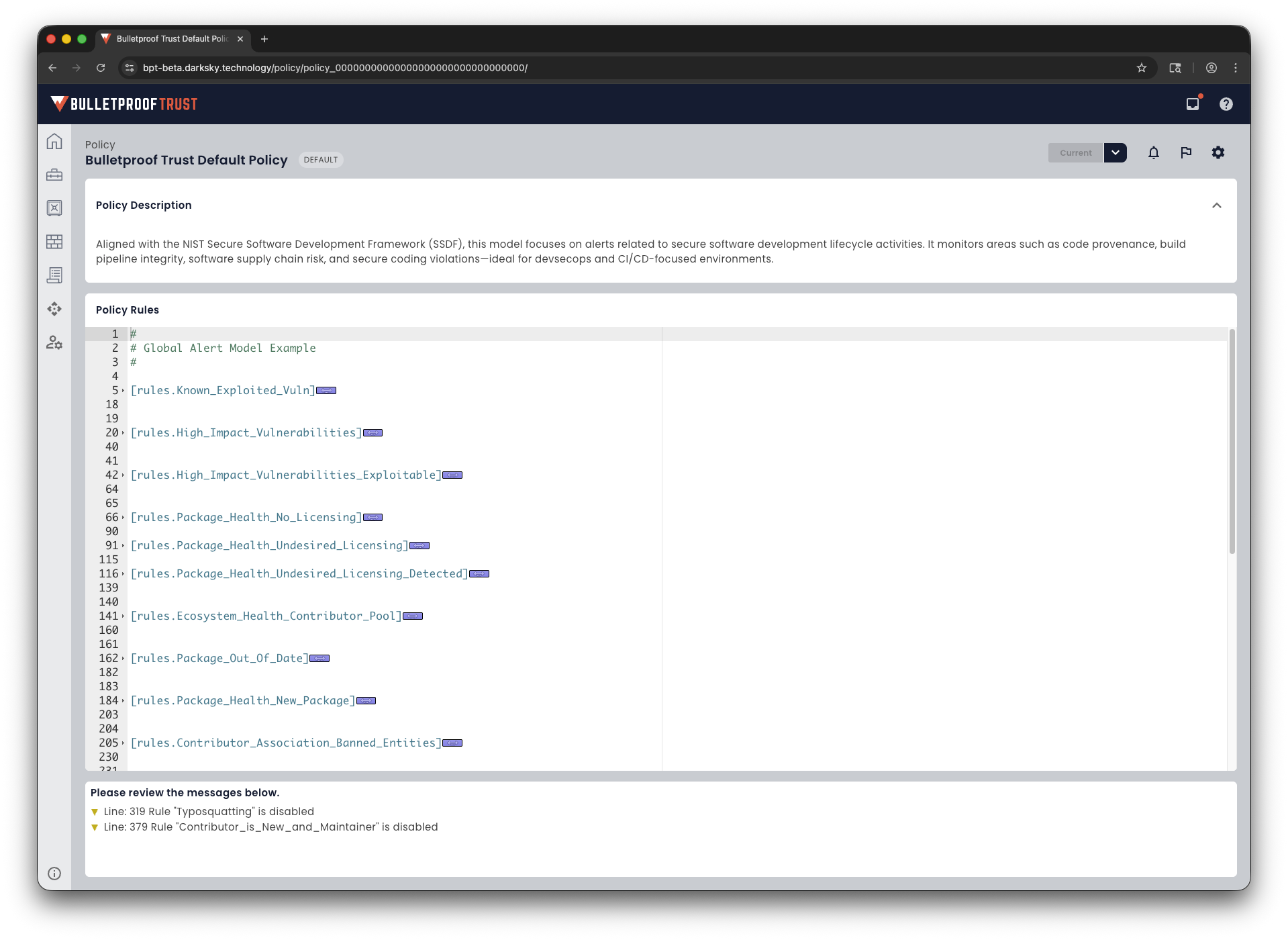
Store pre-canned and custom policies in one place with the Bulletproof Trust Policy Library
Customizable policies with the Bulletproof Trust Policy Editor
Only show the risks that matter to you. Risks that are defined in your policies.
It’s the choice for teams drowning in false-positives.
Trusted by our nations best agencies, and deployable in sensitive air-gapped environments.
You can trust us… But you don’t have to.
You Can Trust Us… But You Don’t Have To
Your code is sensitive, and you can’t share it with anyone. Bulletproof Trust can deploy in air-gapped environments, so you don’t have to share anything with us.
Deploy Air-Gapped
Personally identifiable information (PII) comes with a whole separate set of rules, regulations, and laws. Bulletproof Trust masks every bit of data so you never have to handle PII.
Avoid Dealing with PII
Connect directly to the API to perform all analysis, manage the platform, and integrate with your build environment. Or, drive Bulletproof Trust from the command-line with included CLI tools.
API First, CLI Enabled
Bulletproof Trust has been assessed and found awardable by the Chief Digital and Artificial Intelligence (CDAO) office and the Air Force Platform One Marketplace team.
Trusted by our Best Agencies
TRL9
Bulletproof Trust is Technology Readiness Level 9 (TRL9), deployed by government entities and commercial enterprises in SaaS, on-prem, private-cloud, and air-gapped environments.
Deployed and Battle Tested
Bulletproof Trust integrates with artificial intelligence large language models (AI LLM) through the Model Context Protocol (MCP). Get answers and deep insights on your risk data.
AI LLM Integrated
Bulletproof Trust is a 100% US owned and operated company developed by 100% US citizens, cleared or clearable.
100% US-Citizens
No complex calculations. No API call or user tracking. Our pricing is transparent, simple to understand, scalable across the smallest projects to the largest enterprises.
Transparent Pricing