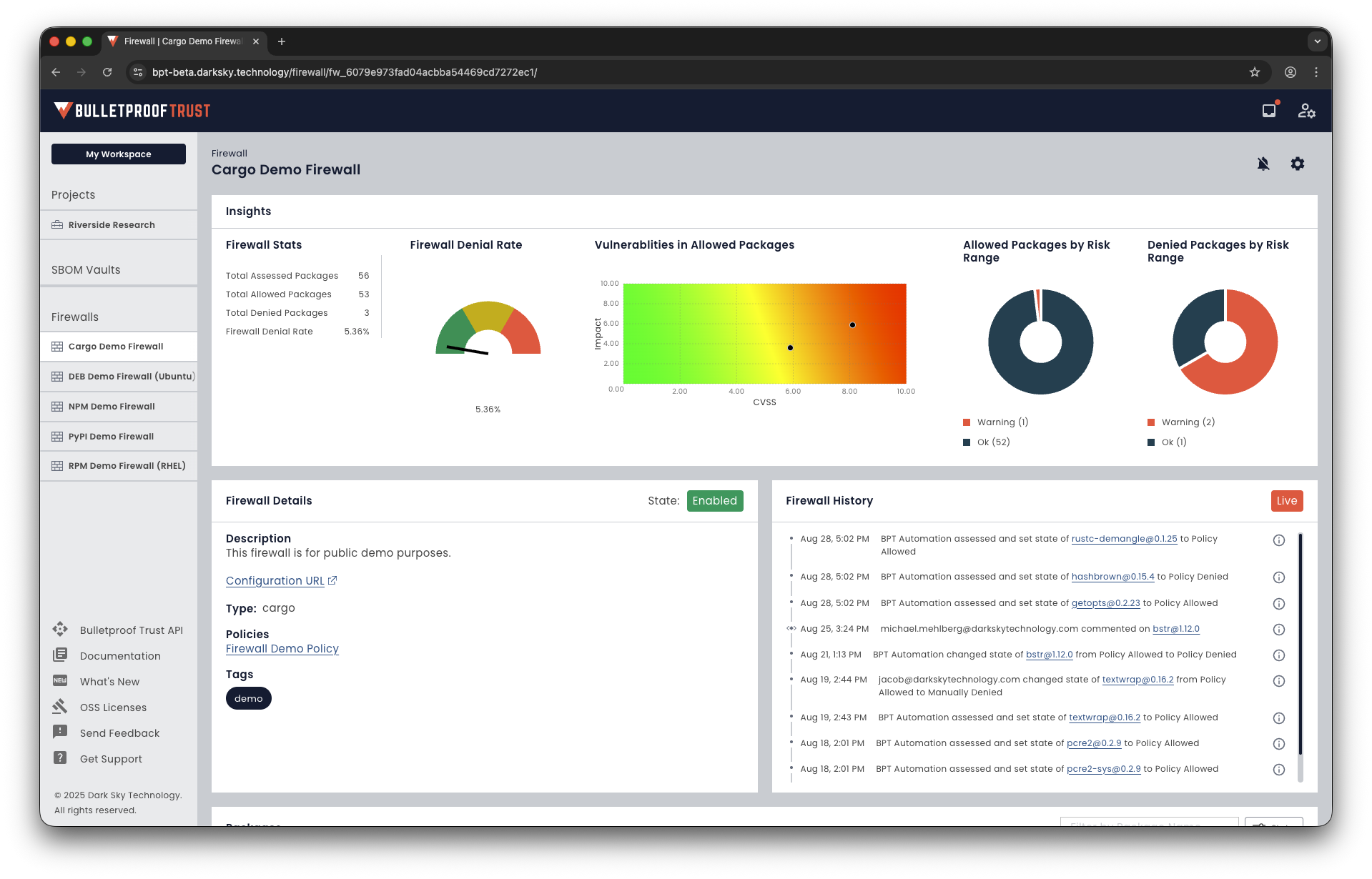
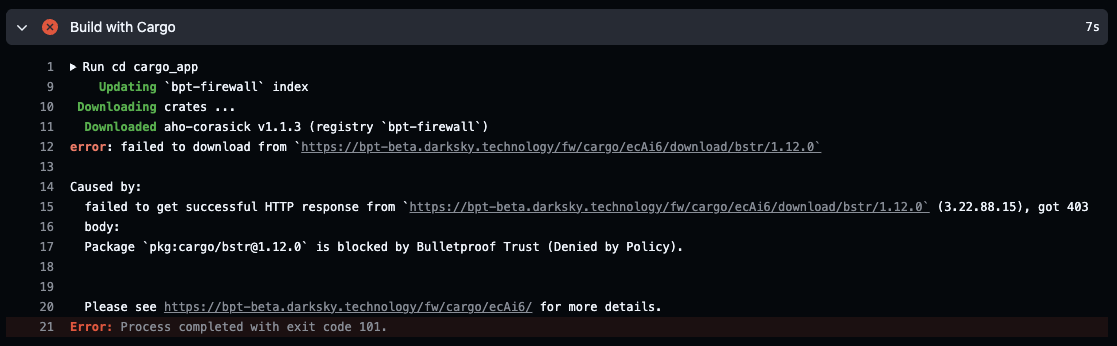
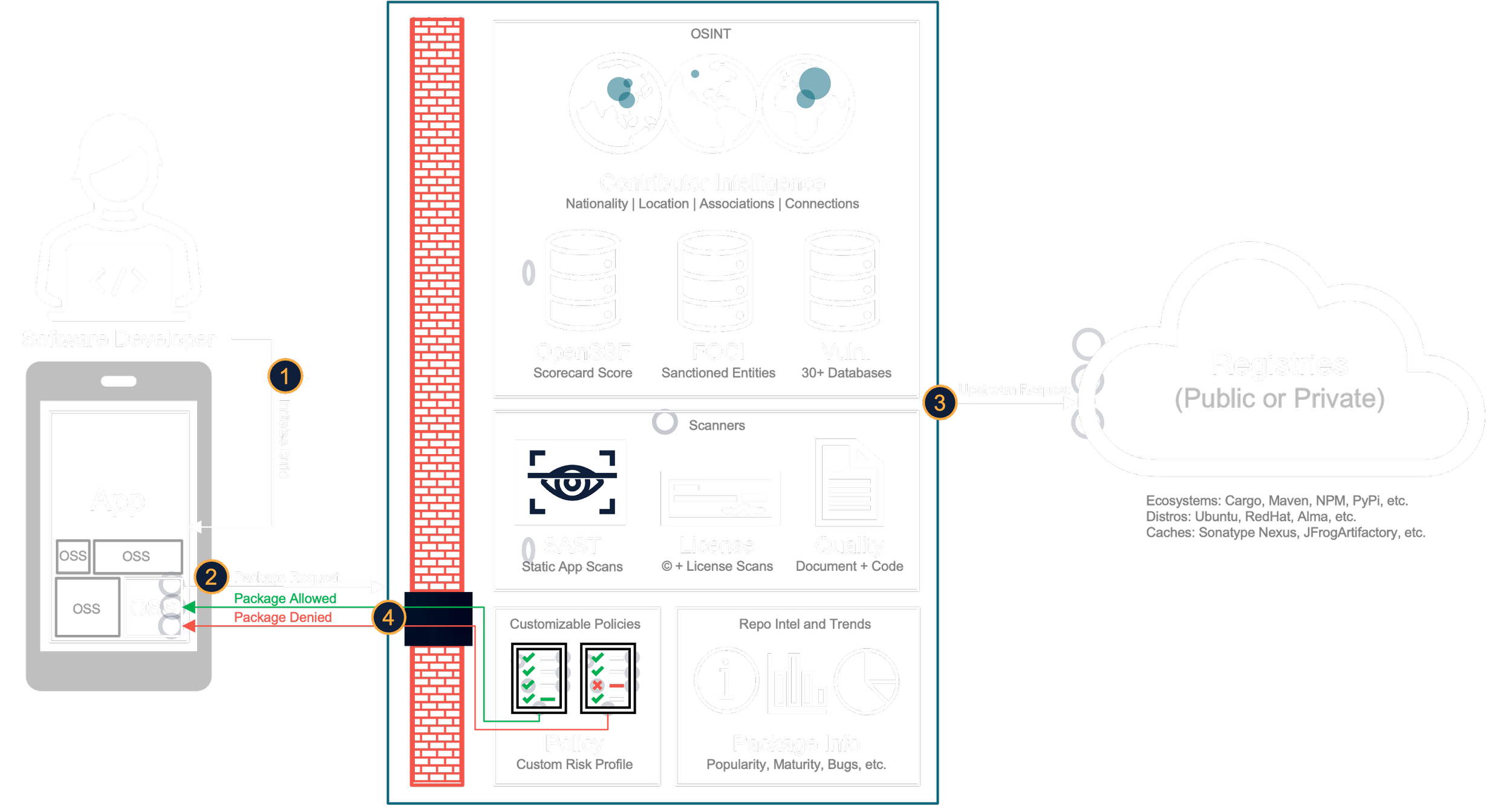
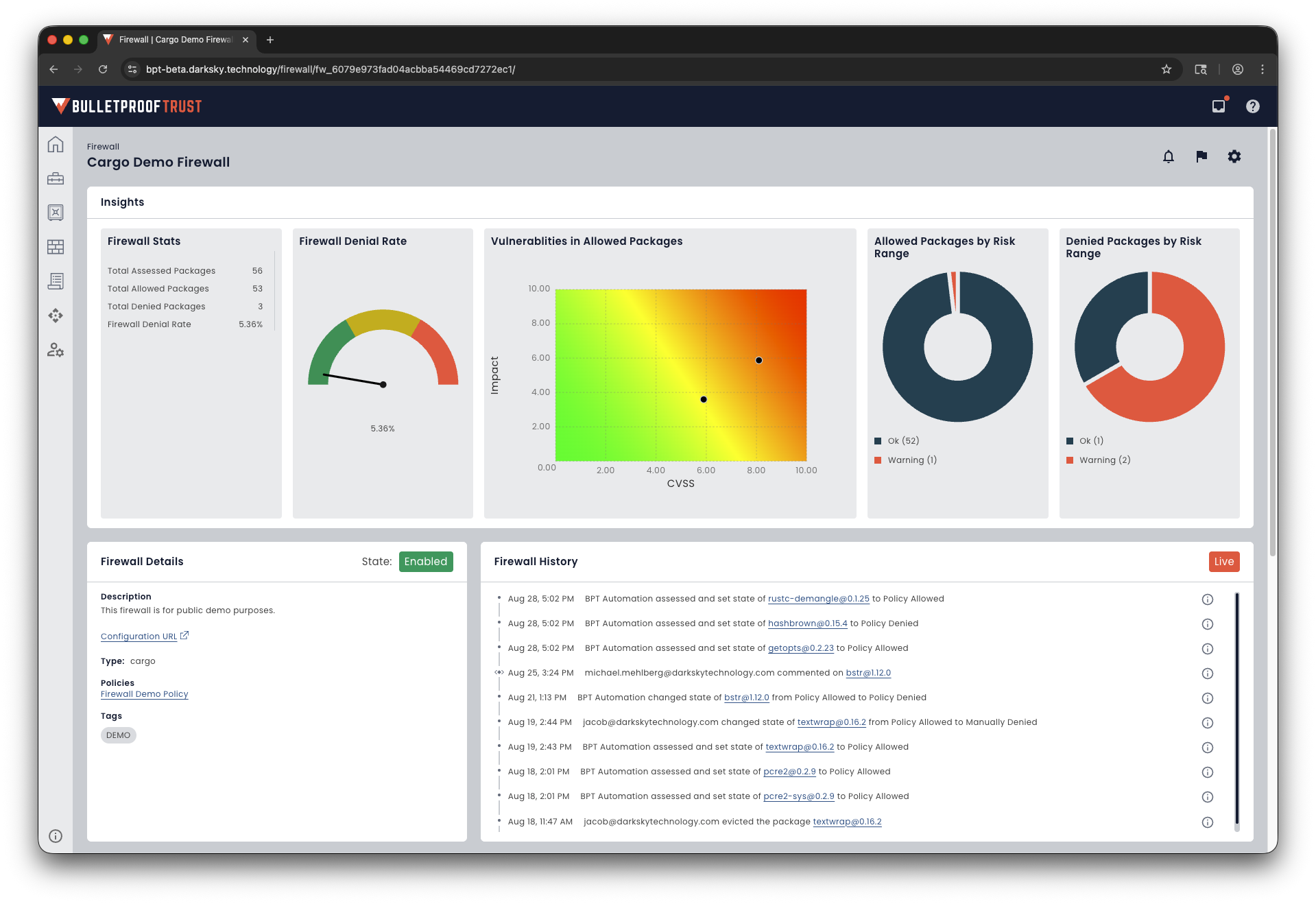
Enforce software supply chain trust policies at the point of development. Block risky contributors, vulnerable packages, and incompatible licenses before they enter your pipeline.
It’s the Black Duck replacement everyone’s been waiting for…
It’s Hard Not to Talk About…
Bulletproof Trust Firewall™ is a novel way to protect software organizations.
When they see it in action, they can’t help but say great things about it:
“Bulletproof Trust stands out as one of the few tools offering any visibility into foreign influence over the software supply chain, a capability not currently claimed by other open-source tools.” — Jim B.
“These folks are the real deal (all intel community) and have built some very impressive capabilities to address the national security concerns surrounding software supply chains.” — Jeff G.
“If I were to build a dashboard for supply chain risk, this would be it.” — Rich M.

Your Build, Your Rules
Manually block or allow packages.
Automatically enforce your policies on every dependency.
Keep your software supply chain clean, compliant, and under your control.


Trusted by our nations best agencies, and deployable in sensitive air-gapped environments.
You can trust us… But you don’t have to.
You Can Trust Us… But You Don’t Have To
Your code is sensitive, and you can’t share it with anyone. Bulletproof Trust can deploy in air-gapped environments, so you don’t have to share anything with us.
Deploy Air-Gapped
Personally identifiable information (PII) comes with a whole separate set of rules, regulations, and laws. Bulletproof Trust masks every bit of data so you never have to handle PII.
Avoid Dealing with PII
Connect directly to the API to perform all analysis, manage the platform, and integrate with your build environment. Or, drive Bulletproof Trust from the command-line with included CLI tools.
API First, CLI Enabled
Bulletproof Trust has been assessed and found awardable by the Chief Digital and Artificial Intelligence (CDAO) office and the Air Force Platform One Marketplace team.
Trusted by our Best Agencies
TRL9
Bulletproof Trust is Technology Readiness Level 9 (TRL9), deployed by government entities and commercial enterprises in SaaS, on-prem, private-cloud, and air-gapped environments.
Deployed and Battle Tested
Bulletproof Trust integrates with artificial intelligence large language models (AI LLM) through the Model Context Protocol (MCP). Get answers and deep insights on your risk data.
AI LLM Integrated
Bulletproof Trust is a 100% US owned and operated company developed by 100% US citizens, cleared or clearable.
100% US-Citizens
No complex calculations. No API call or user tracking. Our pricing is transparent, simple to understand, scalable across the smallest projects to the largest enterprises.
Transparent Pricing