Secure your software supply chain… Not just your code.
Critical systems depends on thousands of third-party components. Each introduces potential risk, from malicious contributors, vulnerabilities, and unmaintained packages to legal and licensing exposure. Bulletproof Trust™ gives you the visibility, control, and assurance you need to manage cyber risk across the entire software supply chain.
“These folks are the real deal (all intel community) and have built some very impressive capabilities to address the national security concerns surrounding software supply chains." Randy H.
〜
"If I were to build a dashboard for supply chain risk, this would be it." Rich M.
〜
"Integrating this tool into your workflow can significantly enhance software supply chain security and risk management efforts." Jim B.
〜
“These folks are the real deal (all intel community) and have built some very impressive capabilities to address the national security concerns surrounding software supply chains." Randy H. 〜 "If I were to build a dashboard for supply chain risk, this would be it." Rich M. 〜 "Integrating this tool into your workflow can significantly enhance software supply chain security and risk management efforts." Jim B. 〜
The Software Supply Chain Challenge
Traditional Software Composition Analysis (SCA) tools only tell you what code is in your stack, not who wrote it or whether it’s trustworthy.
Modern software supply chains demand continuous visibility into:
Open-source contributor trust and behavior.
Package health, maintenance, and deprecation status.
License and legal exposure.
Compliance with NIST SP 800-161 r1, CISA, and Executive Order 14028.
Without this intelligence, organizations risk introducing vulnerabilities, foreign influence, or non-compliant software into mission-critical systems.

The Solution? Bulletproof Trust™
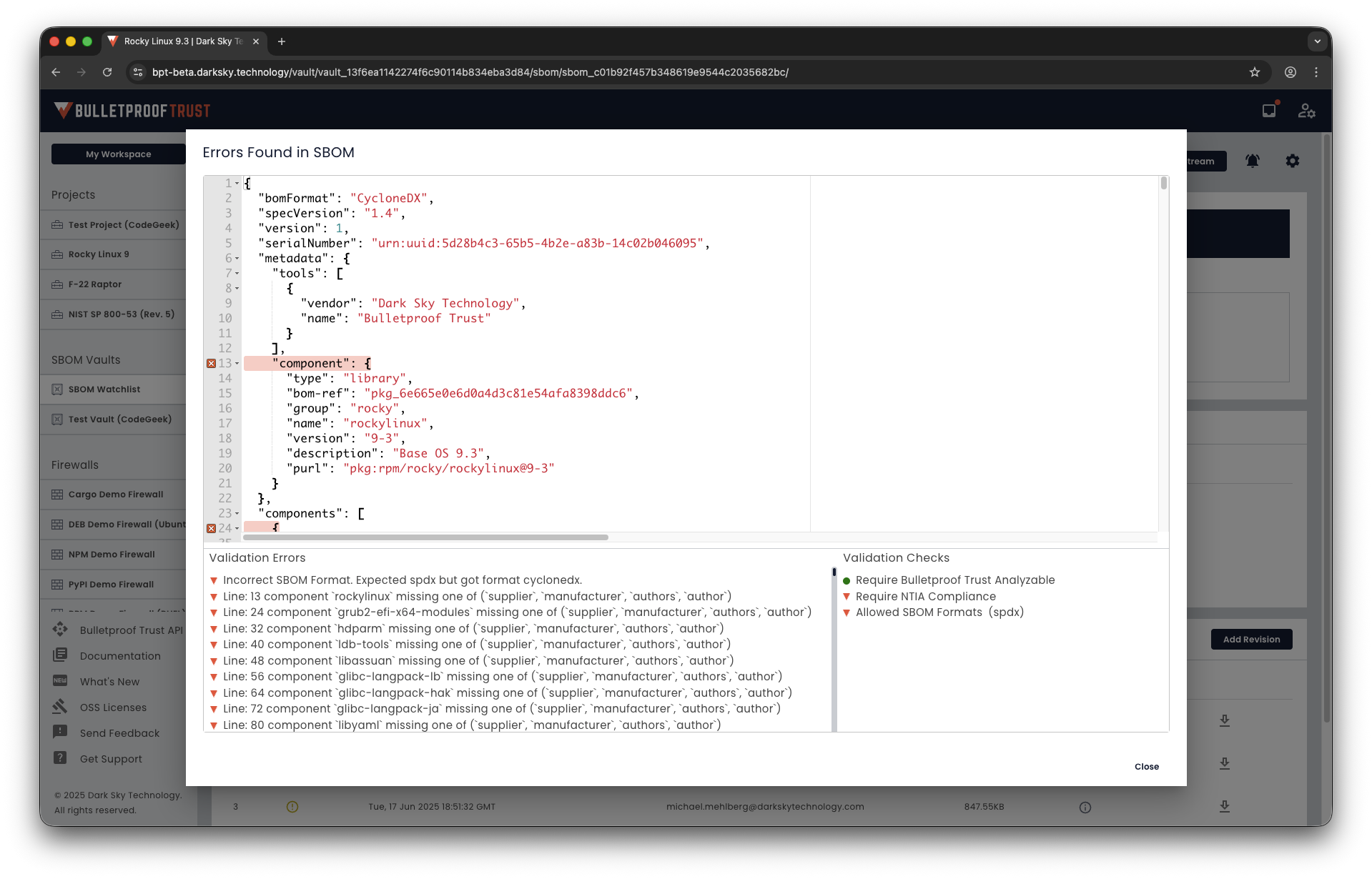
Dark Sky Technology’s Bulletproof Trust is a cyber supply chain risk management (C-SCRM) platform built for regulated and high-security environments. It turns software bill of materials (SBOMs) into actionable intelligence and keeps risky components out of your supply chain.
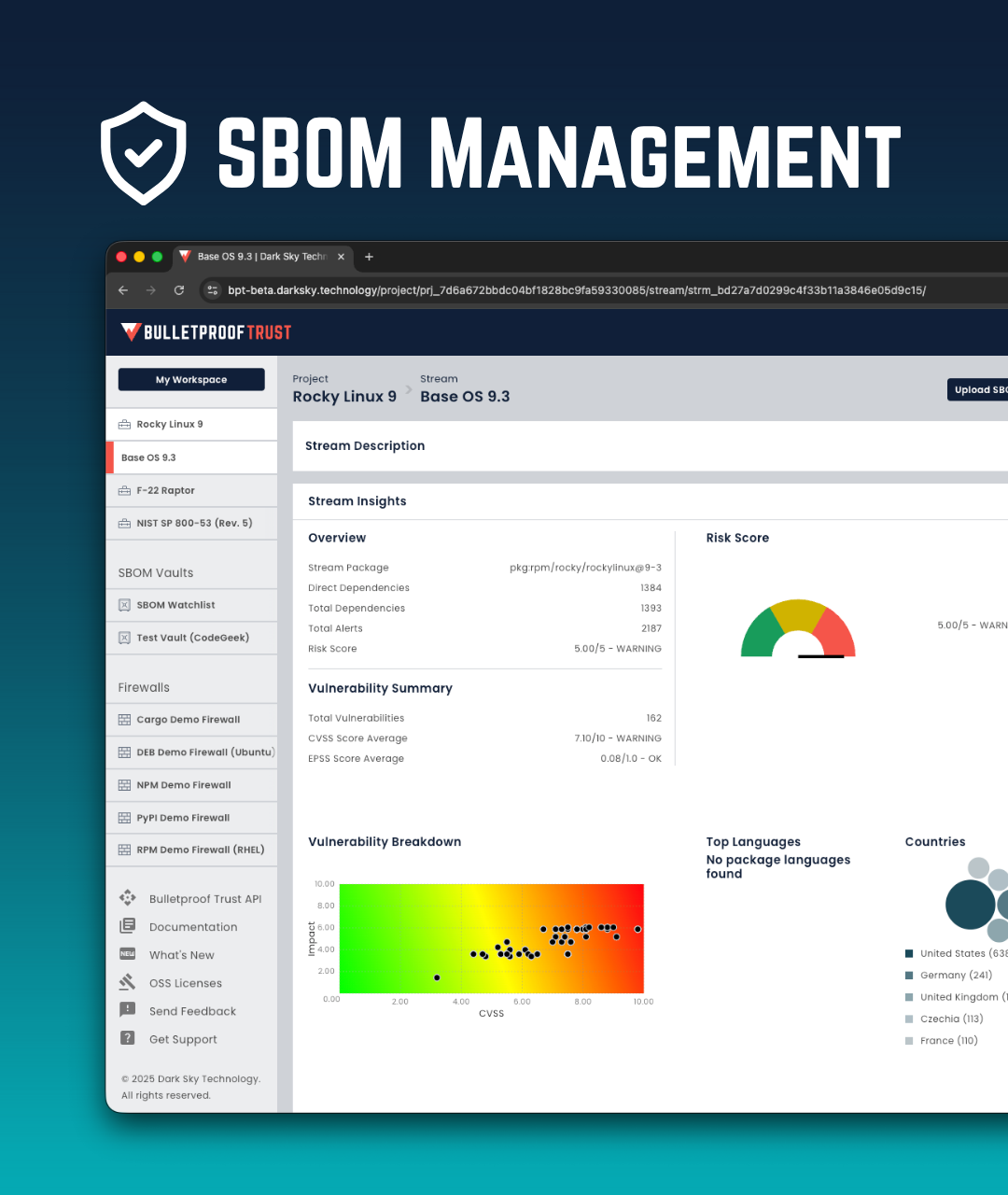
SBOM Management
Securely receive, store, verify, and share SBOMs across projects and programs.
Contributor Risk Analysis
Evaluate contributor identity, nationality, sanction status, and behavioral risk.
Package Health Analysis
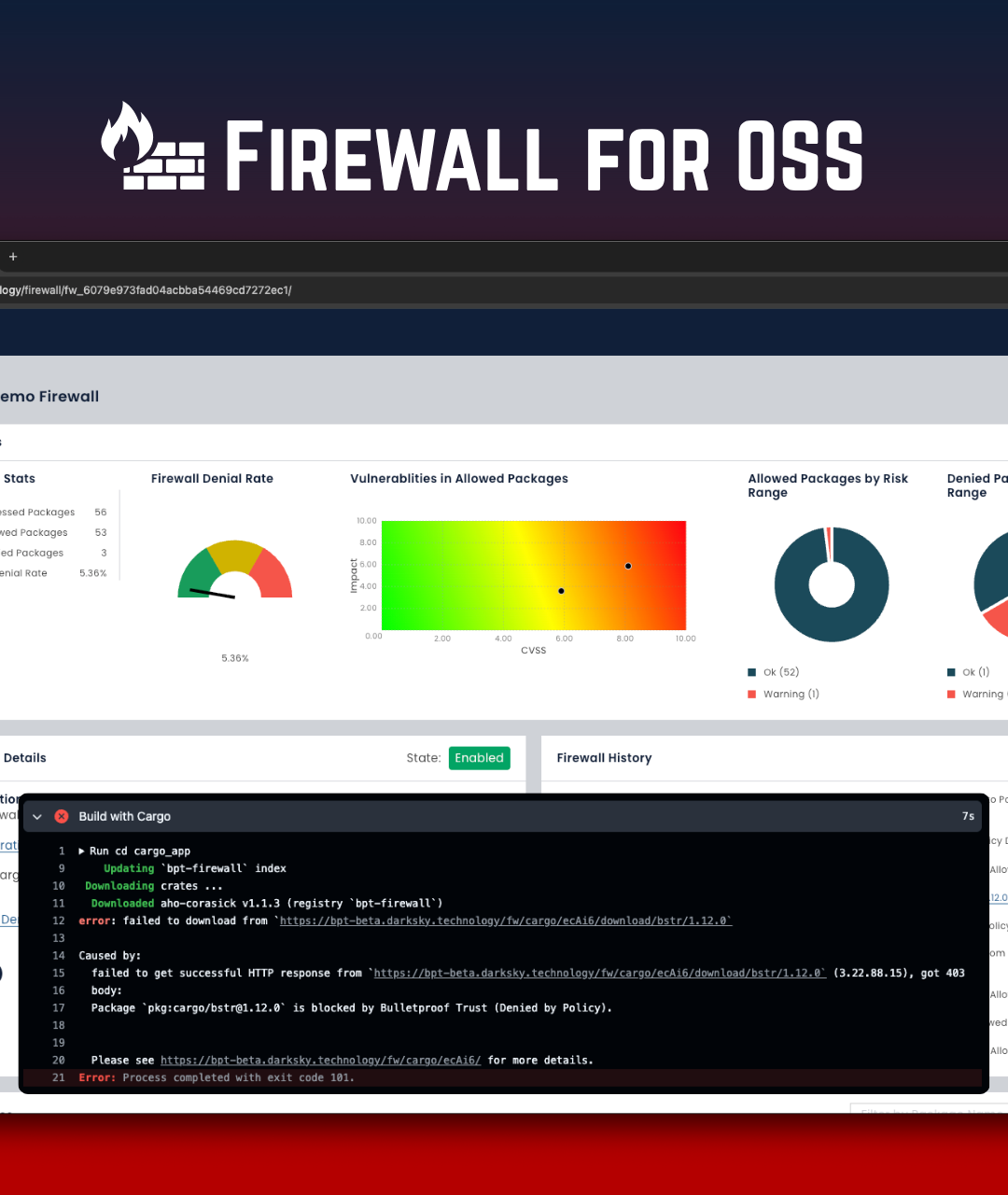
Identify abandoned, deprecated, or vulnerable packages before they reach production.
Trust & Mitigation Engine
Prioritize risks, recommend fixes, and document mitigation decisions.
How it Supports C-SCRM
Aligns with NIST 800-161 r1 and CISA guidance for software assurance and risk reduction.
Enhances SBOM visibility across enterprise and program boundaries.
Strengthens compliance readiness for DoD, DHS, FDA, and other federal mandates.
Provides OSINT-driven threat intelligence for early identification of untrustworthy contributors.

Who Uses Bulletproof Trust?
Dark Sky Technology secures the software that powers our nation’s most critical systems by making trust measurable. Our mission is simple: enable every organization to deploy software they can trust, built from code they can verify.
Defense and aerospace contractors
Federal and healthcare agencies
Software integrators for critical infrastructure
Enterprises adopting DevSecOps at scale
Trusted by our nations best agencies, and deployable in sensitive air-gapped environments.
You can trust us… But you don’t have to.
Take Control of Your Software Supply Chain
Your code is sensitive, and you can’t share it with anyone. Bulletproof Trust can deploy in air-gapped environments, so you don’t have to share anything with us.
Deploy Air-Gapped
Personally identifiable information (PII) comes with a whole separate set of rules, regulations, and laws. Bulletproof Trust masks every bit of data so you never have to handle PII.
Avoid Dealing with PII
Connect directly to the API to perform all analysis, manage the platform, and integrate with your build environment. Or, drive Bulletproof Trust from the command-line with included CLI tools.
API First, CLI Enabled
Bulletproof Trust has been assessed and found awardable by the Chief Digital and Artificial Intelligence (CDAO) office and the Air Force Platform One Marketplace team.
Trusted by our Best Agencies
TRL9
Bulletproof Trust is Technology Readiness Level 9 (TRL9), deployed by government entities and commercial enterprises in SaaS, on-prem, private-cloud, and air-gapped environments.
Deployed and Battle Tested
Bulletproof Trust integrates with artificial intelligence large language models (AI LLM) through the Model Context Protocol (MCP). Get answers and deep insights on your risk data.
AI LLM Integrated
Bulletproof Trust is a 100% US owned and operated company developed by 100% US citizens, cleared or clearable.
100% US-Citizens
No complex calculations. No API call or user tracking. Our pricing is transparent, simple to understand, scalable across the smallest projects to the largest enterprises.
Transparent Pricing